
Access Control System
Our company specializes in delivering cutting-edge Access Control Systems, offering not only secure and streamlined physical access but also optimizing overall operational efficiency. Through a strategic approach that leverages innovation and embraces open solutions, we go beyond conventional measures. Our commitment extends to tailoring highly advanced security protocols, ensuring a precise alignment with the unique and evolving needs of your organization, thus providing a comprehensive and future-ready security solution.


CCTV & Video Management Systems
Neural Tech specializes in CCTV and Video Management Systems, providing advanced solutions for superior surveillance. Our systems feature robust monitoring, utilizing state-of-the-art technology for precise video capture and analysis. Paired with cutting-edge Video Management Systems, we ensure seamless integration, efficient storage, and organized retrieval of footage. Clients rely on Neural Tech for secure, scalable solutions meeting diverse surveillance needs with reliability and precision.

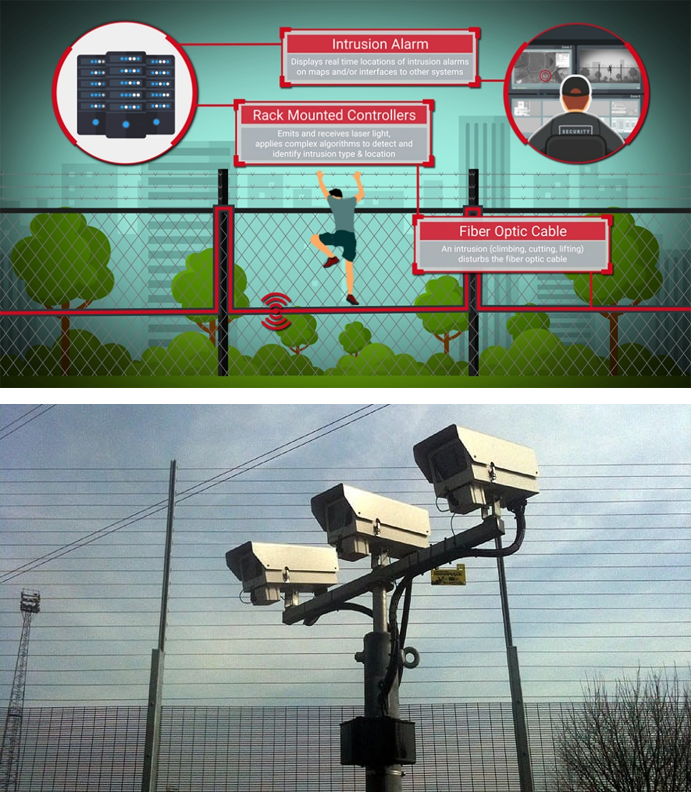
Intrusion Detection Systems (IDS)
Neural Tech offers advanced Intrusion Detection Systems (IDS) to enhance security measures. Our solutions use advanced technologies for prompt threat detection and response. With a focus on precision and reliability, Neural Tech’s IDS offerings provide comprehensive protection, enabling businesses and individuals to safeguard assets effectively. Clients benefit from our expertise in creating tailored IDS solutions, adapting to evolving security challenges with proactive threat detection capabilities.


Perimeter Security Solutions
Neural Tech offers advanced Perimeter Security Solutions to fortify security measures, leveraging cutting-edge technology for robust defenses. Ensuring protection for both physical and digital assets, our solutions emphasize precision and reliability. Neural Tech’s Perimeter Security Solutions provide comprehensive protection, granting businesses and individuals effective control and monitoring capabilities. Clients appreciate our tailored approach, addressing unique security challenges and adapting to evolving threats with proactive and efficient perimeter protection measures.


